IT security breaches
-
Finance
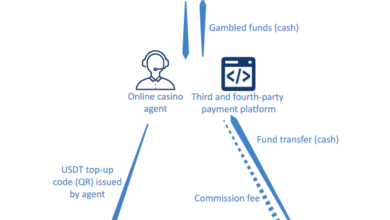
USDT Laundering: $4 Million Stolen in Kenyan Bank Heist
USDT laundering has emerged as a critical issue in recent financial crime cases, notably involving a notorious Kenyan bank heist…
Read More »

USDT laundering has emerged as a critical issue in recent financial crime cases, notably involving a notorious Kenyan bank heist…
Read More »