XRP Price Watch: Volatile Swing Patterns Indicate Caution
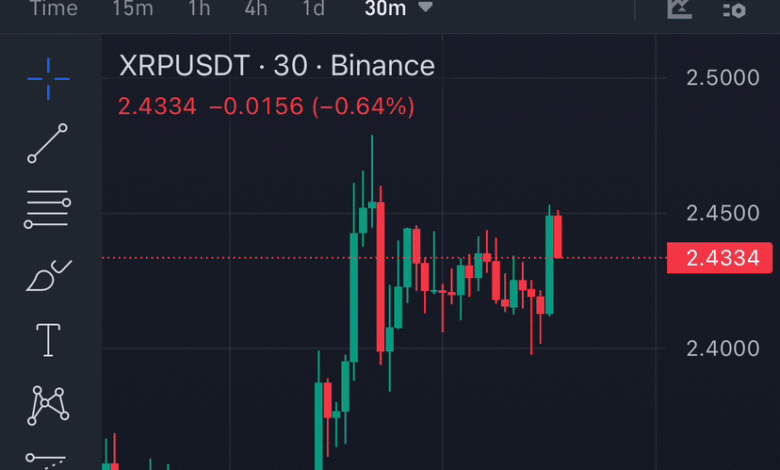
XRP Price Watch is essential for traders looking to navigate the current market landscape effectively. As XRP fluctuates around $2.22 with a significant trading volume, understanding the underlying price analysis, market trends, and chart patterns becomes crucial for making informed trading strategies. Recent fluctuations within a narrow range indicate a compression in volatility, hinting at potential price swings ahead. Traders might find value in utilizing XRP trading strategies that emphasize both short and long positions based on breakout points. Keeping an eye on XRP’s movement will be vital, as any significant shift could trigger a new trading opportunity.
In the realm of digital currencies, closely monitoring XRP’s price trends and market behavior is vital for investors and traders alike. The recent data points, including XRP’s trading activities and the present volatility, suggest an environment ripe for strategic planning. By observing the evolving chart patterns and understanding the implications of short-term movements, participants can develop robust trading tactics. Additionally, the analysis of XRP’s market dynamics will offer insights into broader cryptocurrency trends that could influence potential price actions. This anticipatory watch on XRP serves not only to gauge immediate price shifts but also to align trading strategies with overarching market sentiments.
Understanding XRP Price Analysis
XRP price analysis is critical for traders looking to make informed decisions in the volatile cryptocurrency market. Analyzing price movements, chart patterns, and trading volume provides insights into potential future price actions. As seen in recent trends, the digital asset has shown a tendency for consolidation within specific ranges, often warranted by the fluctuation between $2.20 to $2.24 recently. Recognizing these patterns allows traders to adopt effective XRP trading strategies, helping them identify when to enter and exit their positions successfully.
Moreover, XRP’s recent performance indicates that its price behaviors can be indicative of broader market sentiments. With a market capitalization nearing $131 billion and a trading volume surpassing $1.33 billion, any analysis must consider not just technical indicators but also market trends and news that could impact trading behavior. The consolidation pattern observed might signal upcoming volatility, making it essential to employ tools like moving averages and oscillators for a comprehensive analysis.
XRP Price Watch: Key Market Trends and Volatility
XRP Price Watch includes vital components of the market, particularly understanding its volatility trends. The historical price data reveals that XRP tends to move within predictable ranges, making it a focal point for traders employing various trading strategies. Currently, the fluctuating price range indicates a low volatility environment, which usually precedes significant price moves. Traders need to be vigilant during such times, prepared for potential breakouts either above $2.26 or drops below $2.196, which could set the stage for severe volatility.
Market trends surrounding XRP have shown a bullish structure on the daily chart despite some short-term weaknesses. The formation of lower highs on the 4-hour chart underscores the necessity for caution as traders navigate these waters. Understanding XRP’s market trends not only aids individual trading strategies but also impacts broader trading psychology, influencing how other cryptocurrencies are perceived. This interconnectedness is why XRP price trends serve as a benchmark for many crypto traders.
XRP Trading Strategies During Consolidation Phases
When XRP enters a consolidation phase, traders must adapt their trading strategies effectively to capitalize on the range-bound movements. For example, recent price analysis suggests employing scalping tactics — buying near the lower boundary at $2.20 and selling near the upper range at approximately $2.26. These strategies thrive in low volatility while waiting for confirmation of breakout movements that can lead to more significant profit opportunities. Traders should remain mindful of volume trends, as higher volumes accompanying price movements can confirm the validity of these breakouts.
In addition to scalping, other techniques can be implemented during these phases. For example, swing trading strategies might focus on capturing larger price movements post-breakouts. After observing patterns such as rounded tops or bottoms, traders can position themselves favorably once breakouts are confirmed — entering long positions after a significant price move above established resistance levels. Utilizing tools such as Fibonacci retracement can also help gauge potential reversal points, adding another layer of strategy during these times of consolidation.
Technical Indicators in XRP Chart Patterns
Technical indicators play a critical role in analyzing XRP chart patterns, particularly during volatile market conditions. Indicators such as the Relative Strength Index (RSI), Moving Average Convergence Divergence (MACD), and oscillators provide valuable insights into the current market dynamics. For instance, an RSI reading at 52.45 suggests that XRP is currently neither overbought nor oversold, indicating a consolidation phase that may soon lead to significant price movements.
In addition to oscillators, moving averages—be it simple or exponentially weighted—offer clarity on trends. Short-term averages might suggest bullish momentum, while long-term indicators might show mixed signals, revealing potential resistance levels. Understanding these patterns enables traders to time their entries and exits more effectively, ensuring they take advantage of favorable market conditions while minimizing risks associated with volatility in XRP prices.
XRP Volatility: Preparing for Upcoming Fluctuations
XRP volatility can present both opportunities and challenges for traders. The recent market conditions indicate a compression phase, often setting the stage for upcoming price movements. Monitoring volatility indicators and understanding historical price movements are essential for forecasting potential swings. Traders should prepare for both bullish and bearish scenarios. If the price breaks above $2.26, volumes will be a crucial confirmation signal indicating strength or a bullish breakout. Conversely, falling below the $2.20 level might present traders with a compelling short opportunity.
As XRP navigates through this volatility, keeping up with fundamental news and market sentiment is just as important. Global market dynamics can influence XRP’s performance, and unforeseen events or announcements can lead to sudden price shifts. Having strategies in place that encompass various scenarios not only helps traders manage risk but also enhances their chances of capitalizing on sudden volatility driven by market events or changes in trader sentiment.
The Future of XRP: Price Projections and Market Sentiment
Looking ahead, XRP’s price projections will be shaped by both technical analysis and overall market sentiment. Currently, as XRP has maintained above $2.20, bullish trends suggest that the asset may attempt to retest its previous highs around the resistance zone of $2.34. Analysts who incorporate market trend analysis into their projections often highlight the importance of volume in confirming these movements. Should XRP manage to solidify above $2.30, a broader market rally could ensue, positioning it favorably against competitors.
However, it is vital to balance bullish expectations with realistic assessments of market sentiments. With oscillators indicating overbought conditions on shorter timeframes, there remains a caution against chasing prices too eagerly. A reversal could lead traders back towards $2.15, making it crucial for investors to monitor market indicators closely. Overall, maintaining a comprehensive understanding of XRP’s price behavior, supported by market trends, will be instrumental in making sound trading decisions.
XRP’s Performance Relative to Other Cryptocurrencies
When considering XRP’s performance, it’s beneficial also to analyze it relative to other cryptocurrencies. As part of a broader portfolio strategy, understanding how XRP interacts with leading assets like Bitcoin and Ethereum can provide traders with deeper insights into market dynamics. For instance, if Bitcoin experiences a downturn, XRP’s price may also react, depending on overall market sentiment.
Additionally, examining XRP through the lens of trading volume can shed light on market interest relative to its peers. The high trading volume of $1.33 billion indicates robust participation, perhaps a result of XRP’s established position in the altcoin market. By observing market conditions in relation to other cryptocurrencies, traders can fine-tune their strategies, identifying potential entry and exit points while mitigating risks associated with market volatility.
Risk Management in XRP Trading
Risk management is essential when trading XRP, especially in a market characterized by high volatility. Traders must set clear stop-loss levels to protect their capital during unforeseen price swings. Monitoring price levels such as $2.20 and $2.196, where breakouts can lead to significant losses, is crucial for implementing effective risk management strategies. This approach includes sizing trades appropriately, ensuring that a single loss does not disproportionately affect the overall trading portfolio.
Furthermore, diversifying across different cryptocurrencies can also serve as a cushion against market volatility. By not putting all capital into XRP alone, traders can spread their risk and potentially benefit from varied performance across different assets. Establishing a disciplined trading plan with defined risk metrics will ensure that traders can navigate XRP’s fluctuations without succumbing to emotional decision-making.
Frequently Asked Questions
What trends should I watch in XRP price analysis this week?
In this week’s XRP price analysis, traders should focus on consolidation phases, particularly the range between $2.20 and $2.26. This compression zone often foreshadows significant moves. Watch for breakout confirmations, which could signal bullish or bearish trades.
How can I implement effective XRP trading strategies?
To develop effective XRP trading strategies, consider scalping within the current range of $2.20 to $2.26. Buying near the lower boundary and selling at the upper side can maximize short-term gains until a breakout occurs, along with keeping an eye on volume trends for confirmation.
What are the recent XRP market trends indicating?
Recent XRP market trends are reflecting a mixture of bullish sentiment on the daily chart and cautious short-term weakness on the 4-hour chart. It’s crucial to monitor the $2.30 resistance zone, as breaking above it with significant volume may drive XRP prices higher.
What XRP chart patterns are crucial for short-term trading?
Crucial XRP chart patterns for short-term trading include the formation of rounding tops and consolidation ranges. Currently, patterns suggest a potential for both bullish breakout above $2.26 and bearish signals if prices drop below $2.196.
How does XRP volatility affect trading decisions?
XRP volatility can have significant effects on trading decisions. Traders must be vigilant during consolidation periods, where low volatility can precede large price swings. Staying aware of potential breakout points around $2.20 and $2.26 will be essential for effective trading.
| Key Point | Details |
|---|---|
| Current Price | $2.22 as of July 5, market cap at $131 billion. |
| Trading Volume | 24-hour volume recorded at $1.33 billion. |
| Intraday Range | Fluctuates between $2.20 and $2.24. |
| Weekly Range | Trades between $2.17 and $2.30. |
| 1-Hour Chart Analysis | Consolidation phase between $2.196 and $2.26, suggesting potential breakout above or bearish below. |
| 4-Hour Chart Patterns | Signs of weakness with a rounded top formation indicating potential for downside. |
| Daily Chart Trends | Structurally bullish but needs to maintain above $2.20 to avoid a bearish scenario. |
| Oscillator Status | Mostly neutral, indicating indecision in the market. |
| Moving Averages Overview | Short-term MAs are bullish, while longer-term indicators are mixed. |
| Bullish Outlook | Breakout above $2.30 could lead to $2.34 and higher. |
| Bearish Outlook | Breakdown below $2.20 may target $2.15, exposing further downside risk. |
Summary
XRP Price Watch reveals that XRP is currently experiencing a crucial phase, trading at $2.22, which showcases both bullish and bearish sentiment in the market. Traders should prepare for potential volatility as the asset is testing key support and resistance levels, making it essential to monitor for breakout opportunities or possible reversal signals. Being aware of these patterns will be fundamental in navigating your trading strategies effectively.